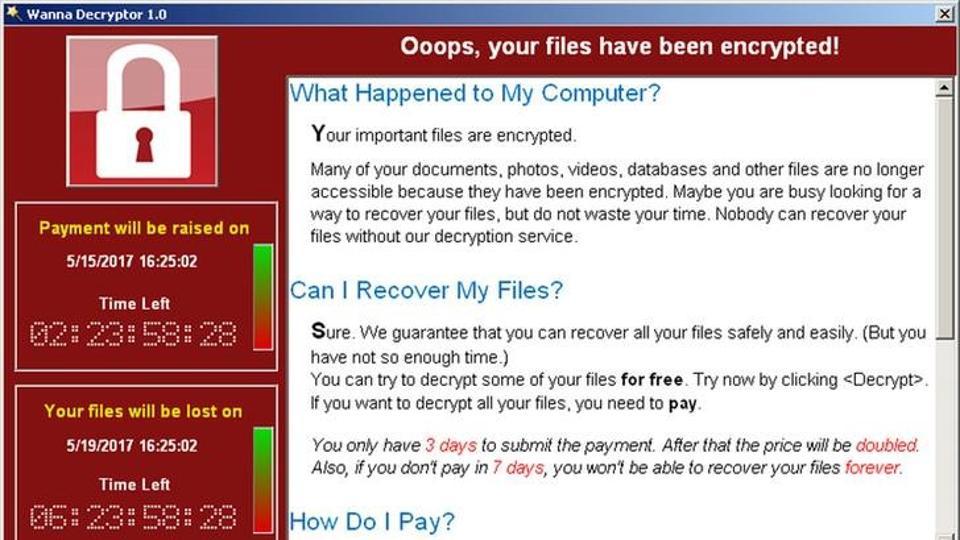
WannaCry the biggest ransomware attack in internet history
On Friday, a few healing facilities in the United Kingdom were hit with an impossible to miss assault: PCs assumed control, information inside encoded and held payment, for the measly installment of just $300. The assault spread quickly, hitting 150 nations and closing down everything from telecoms in Spain to the Interior Ministry in Russia. And after that, through a stroke of good fortune, the WanaCryptor assault was slowed down in its tracks, a killswitch found by luck in the nick of time for the end of the week. What, precisely would we say we are to make of the biggest ransomware assault ever?
The worm, referred to differently as WannaCry, WanaCryptor, and WannaCrypt, targets PCs running Microsoft working frameworks. It is based on an endeavor named EternalBlue, one of numerous NSA "digital weapons" discharged by a gathering known as the Shadow Brokers, who initially began spilling NSA apparatuses late the previous summer.
Not at all like phishing or spearphishing assaults, where a PC is traded off in light of the fact that a client snaps a connection in a focused on email, WannaCry works without misusing any human blunder.
Kasperksey Lab, a notable cybersecurity organization, wrote in a lavishly point by point FAQ about the assault that "Maybe the primary motivation behind why Wannacry was so fruitful is the way that the EternalBlue misuse works over the Internet without requiring any client cooperation." Because it strikes over systems, it can at present wreak destruction inside a nearby system even with the killswitch dynamic, as the killswitch needs the web to work.
Before WannaCry spreads, it verifies whether it can associate with a particular area. In the event that the space is enrolled and possessed, it's done, and continues no further. On the off chance that it neglects to interface, then WannaCry spreads as it was intended to do, tainting machines and requesting buy-off.
The killswitch was found by a youthful PC security specialist in the United Kingom, who enlisted the area indicated in the WannaCry programming, and after that directed activity to it to a sinkhole server, implied for catching botnets. This security specialist composed an incredible review of the experience of getting WannaCry, which is here.
For his inconvenience, the pseudonymous specialist then had his character uncovered by British sensationalist newspapers. One motivation to be pseudonymous is to make it less demanding to complete security work without turning into a particular focus for the sort of individuals whose assaults he is attempting to stop. That matters particularly with WannaCry, in light of the fact that future forms of the ransomware (some of which may as of now be live and in the wild) may exclude the killswitch, which will make them harder to stop.
Microsoft discharged patches for the powerless working frameworks that can keep the present rendition of WannaCry from tainting fixed PCs. The main fix that secures against assaults like this was discharged in March, however not each client naturally downloads and introduces all patches or programming refreshes. Microsoft responsively discharged a fix for Windows XP, a 16-year-old working framework that is at no time in the future formally bolstered, yet still utilized as a part of numerous PCs. (Microsoft additionally discharged patches for two other working frameworks still just in "client bolster," Windows 8, and Windows Server 2003). In client direction discharged about the assault, Microsoft prescribes consequently refreshing as a proactive measure.
Cisco's Talos risk checking and assurance group additionally prescribes blocking TOR leave hubs so that WannaCry can't spread into an association through the steering anonymization instrument. Past that, the Talos suggestions incorporate industry best practices like just utilizing working frameworks that are effectively upheld and get security refreshes, convenient security fixing, running hostile to malware programming, and particularly, having an arrangement for calamities with information routinely went down and put away in gadgets that are kept disconnected. The more excess information put away where programmers can't get to it, the less convincing it is for individuals to pay emancipate.
WannaCry worked due to a perplexing jumble of conditions. The accessibility of bitcoin as an approach to pay payoffs to mysterious offenders unquestionably helped, as did the adventure created by the NSA itself. Both occurred in a setting where individuals associations still utilize old programming, and it's simple for organizations like Microsoft to move accuse onto the NSA for making the adventure and on clients for not fixing security.
"Innovation is dispatched so brimming with openings that a tremendous piece of the business is a gigantic group of exceedingly prepared experts working level out to attachment every one of the holes, composes cybersecurity analyst Stilgherrian. "At that point, when clients unavoidably slip and sink into in this deluge of deficiencies, the merchants and cybersecurity experts censure them for being not able swim."
Or, on the other hand, as the proprietor of Pinboard (who Stilgherrian cites) put it all the more briefly:
Put all the more liberally, the associations that purchase innovation need to put it to use for its expected reason, and frequently don't have the financial plan or aptitude to ensure that any given innovation does its expressed occupation and doesn't have any security defects. As we noted when WannaCry spread on Friday, security scientists found the NHS utilizing obsolete programming back in November. Settling that product isn't simply a question of finding another working framework, it's finding and introducing one that won't break the current framework, then preparing everybody who needs to utilize it how to do as such, and afterward trusting that the new programming won't wind up noticeably obsolete. Consistent security is costly for everyone, except particularly so for end-clients. Furthermore, when things turn out badly, it can cost countless dollars, all moved onto the back of the product purchasers, and not the product creators.
the biggest ransomware attack in internet history
It depended on a spilled NSA "digital weapon"
The worm, referred to differently as WannaCry, WanaCryptor, and WannaCrypt, targets PCs running Microsoft working frameworks. It is based on an endeavor named EternalBlue, one of numerous NSA "digital weapons" discharged by a gathering known as the Shadow Brokers, who initially began spilling NSA apparatuses late the previous summer.
It spread without misusing client communications
Not at all like phishing or spearphishing assaults, where a PC is traded off in light of the fact that a client snaps a connection in a focused on email, WannaCry works without misusing any human blunder.
Kasperksey Lab, a notable cybersecurity organization, wrote in a lavishly point by point FAQ about the assault that "Maybe the primary motivation behind why Wannacry was so fruitful is the way that the EternalBlue misuse works over the Internet without requiring any client cooperation." Because it strikes over systems, it can at present wreak destruction inside a nearby system even with the killswitch dynamic, as the killswitch needs the web to work.
Drink water to be fit and healthy Know more
The killswitch was a basic URL check
Before WannaCry spreads, it verifies whether it can associate with a particular area. In the event that the space is enrolled and possessed, it's done, and continues no further. On the off chance that it neglects to interface, then WannaCry spreads as it was intended to do, tainting machines and requesting buy-off.
The killswitch was found by a youthful PC security specialist in the United Kingom, who enlisted the area indicated in the WannaCry programming, and after that directed activity to it to a sinkhole server, implied for catching botnets. This security specialist composed an incredible review of the experience of getting WannaCry, which is here.
For his inconvenience, the pseudonymous specialist then had his character uncovered by British sensationalist newspapers. One motivation to be pseudonymous is to make it less demanding to complete security work without turning into a particular focus for the sort of individuals whose assaults he is attempting to stop. That matters particularly with WannaCry, in light of the fact that future forms of the ransomware (some of which may as of now be live and in the wild) may exclude the killswitch, which will make them harder to stop.
It gone after un-fixed PCs
Microsoft discharged patches for the powerless working frameworks that can keep the present rendition of WannaCry from tainting fixed PCs. The main fix that secures against assaults like this was discharged in March, however not each client naturally downloads and introduces all patches or programming refreshes. Microsoft responsively discharged a fix for Windows XP, a 16-year-old working framework that is at no time in the future formally bolstered, yet still utilized as a part of numerous PCs. (Microsoft additionally discharged patches for two other working frameworks still just in "client bolster," Windows 8, and Windows Server 2003). In client direction discharged about the assault, Microsoft prescribes consequently refreshing as a proactive measure.
Cisco's Talos risk checking and assurance group additionally prescribes blocking TOR leave hubs so that WannaCry can't spread into an association through the steering anonymization instrument. Past that, the Talos suggestions incorporate industry best practices like just utilizing working frameworks that are effectively upheld and get security refreshes, convenient security fixing, running hostile to malware programming, and particularly, having an arrangement for calamities with information routinely went down and put away in gadgets that are kept disconnected. The more excess information put away where programmers can't get to it, the less convincing it is for individuals to pay emancipate.
Keeping and recouping from this sort of assault is costly and muddled
WannaCry worked due to a perplexing jumble of conditions. The accessibility of bitcoin as an approach to pay payoffs to mysterious offenders unquestionably helped, as did the adventure created by the NSA itself. Both occurred in a setting where individuals associations still utilize old programming, and it's simple for organizations like Microsoft to move accuse onto the NSA for making the adventure and on clients for not fixing security.
"Innovation is dispatched so brimming with openings that a tremendous piece of the business is a gigantic group of exceedingly prepared experts working level out to attachment every one of the holes, composes cybersecurity analyst Stilgherrian. "At that point, when clients unavoidably slip and sink into in this deluge of deficiencies, the merchants and cybersecurity experts censure them for being not able swim."
Or, on the other hand, as the proprietor of Pinboard (who Stilgherrian cites) put it all the more briefly:
Put all the more liberally, the associations that purchase innovation need to put it to use for its expected reason, and frequently don't have the financial plan or aptitude to ensure that any given innovation does its expressed occupation and doesn't have any security defects. As we noted when WannaCry spread on Friday, security scientists found the NHS utilizing obsolete programming back in November. Settling that product isn't simply a question of finding another working framework, it's finding and introducing one that won't break the current framework, then preparing everybody who needs to utilize it how to do as such, and afterward trusting that the new programming won't wind up noticeably obsolete. Consistent security is costly for everyone, except particularly so for end-clients. Furthermore, when things turn out badly, it can cost countless dollars, all moved onto the back of the product purchasers, and not the product creators.



Comments
Post a Comment